I spent some time this week at work trying to get a correct setup in querying the (Sentinel) Log Analytics store from a Logic App in Microsoft Azure. So I thought it would be good idea to document it for myself and others. :)
The problem
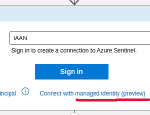
Logic Apps allow you to perform actions in Microsoft and 3rd party services. The integration in Logic Apps sometimes supports the use of System-assigned Managed Identities and sometimes they don’t. As you can guess, when you want to query a Log Analytics store, it doesn’t.
How it should be
The connection from a Logic App to Sentinel actions can use a System-assigned Managed Identity. Making it easy and hands-off for everyone involved.
Connecting to Azure Log Analytics (Azure Monitor)
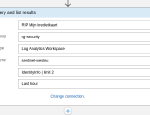
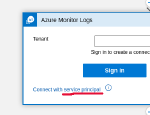
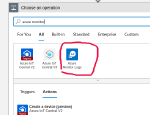
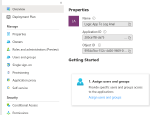
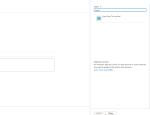
If you search for “Azure Monitor” when creating a new block in your Logic App, you can select the “Run query and list results” action. As you can see from the screenshots, there’s no option to use the Managed Identity of the Logic App.
Creating our own Service Principal
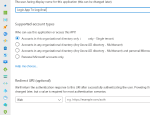
Since we cannot make a User-assigned Managed Identity (same problem), we need to make a normal Service Principal where we do the secret management ourselves. :’( Within Azure a Service Principal is wrapped in an Application. To make an Application, we create an App Registration in our Azure AD of our Azure Tenant.
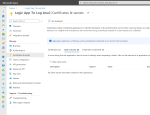
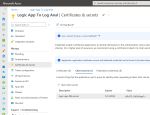
When you register an Application, it will create an Enterprise Application (an instance of your registered App) which contains a Service Principal. Within this Enterprise Application, we’ll create a Secret that can be used to authenticate as the Service Principal.
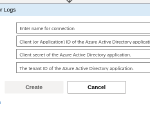
Configuring our Logic App to use the Service Principal
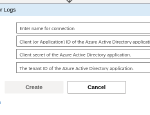
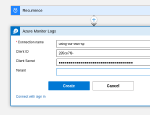
We just need to fill in all the information in the Connector form that we got when we created our Enterprise Application and secret.
And then run it:
Since we haven’t given our Service Principal any rights, it’s unable to execute queries on Log Analytics. That’s what we expect. So let’s give it some rights…
Giving our Service Principal the correct rights
Rights for access are given on the Destination object not the caller, in this case the Log Analytics store.
Let’s go to our Log Analytics store that backs the Azure Sentinel. Within this Log Analytics workspace, we will configure the Access Control (IAM).
And let’s run our Logic App again:

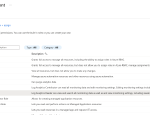
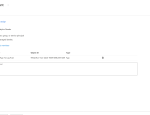
Our Logic App can now query the IdentityInfo table in Log Analytics.
Or a table with some data: